Difference between revisions of "Port 9100 printing"
| Line 2: | Line 2: | ||
Raw printing is what we define as the process of making a connection to port 9100/tcp of a network printer – a functionality which was originally introduced by HP in the early 90s using separate hardware modules. It is the default method used by ''CUPS'' and the ''Windows printing architecture'' <ref>''[https://msdn.microsoft.com/windows/hardware/drivers/print/printer-driver-architecture Windows Printer Driver Architecture]'', Microsoft Corporation</ref> to communicate with network printers as it is considered as `the simplest, fastest, and generally the most reliable network protocol used for printers' <ref>''[https://www.cups.org/doc/network.html\#PROTOCOLS Network Protocols supported by CUPS – AppSocket Protocol]'', M. Sweet</ref>. Raw port 9100 printing, also referred to as ''JetDirect'', ''AppSocket'' or ''PDL-datastream'' actually is not a printing protocol by itself. Instead all data sent is directly processed by the printing device, just like a parallel connection over TCP. In contrast to [[LPD]], [[IPP]] and [[SMB]] interpreted [[Fundamentals#Printer Control Languages|printer control]] or [[Fundamentals#Page Description Languages|page description]] languages can send direct feedback to the client, including status and error messages. Such a '''bidirectional channel''' is not only perfect for debugging, but gives us direct access to results of PJL, PostScript or PCL commands, for example for [information disclosure] attacks. Therefore raw port 9100 printing – which is supported by almost any network printer – is used as the channel for security analysis with [[PRET]] and [[PFT]]. | Raw printing is what we define as the process of making a connection to port 9100/tcp of a network printer – a functionality which was originally introduced by HP in the early 90s using separate hardware modules. It is the default method used by ''CUPS'' and the ''Windows printing architecture'' <ref>''[https://msdn.microsoft.com/windows/hardware/drivers/print/printer-driver-architecture Windows Printer Driver Architecture]'', Microsoft Corporation</ref> to communicate with network printers as it is considered as `the simplest, fastest, and generally the most reliable network protocol used for printers' <ref>''[https://www.cups.org/doc/network.html\#PROTOCOLS Network Protocols supported by CUPS – AppSocket Protocol]'', M. Sweet</ref>. Raw port 9100 printing, also referred to as ''JetDirect'', ''AppSocket'' or ''PDL-datastream'' actually is not a printing protocol by itself. Instead all data sent is directly processed by the printing device, just like a parallel connection over TCP. In contrast to [[LPD]], [[IPP]] and [[SMB]] interpreted [[Fundamentals#Printer Control Languages|printer control]] or [[Fundamentals#Page Description Languages|page description]] languages can send direct feedback to the client, including status and error messages. Such a '''bidirectional channel''' is not only perfect for debugging, but gives us direct access to results of PJL, PostScript or PCL commands, for example for [information disclosure] attacks. Therefore raw port 9100 printing – which is supported by almost any network printer – is used as the channel for security analysis with [[PRET]] and [[PFT]]. | ||
| + | |||
| + | === Who would put a printer on the Internet? === | ||
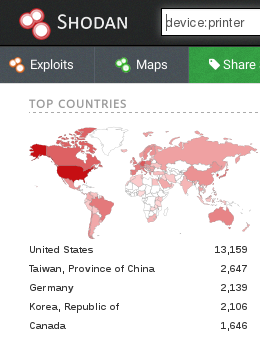
Obviously, a port 9100 based attack requires IP packets to be routed from the attacker to the printer device and backwards but printers usually are not directly connected to the Internet <ref>It however must be noted that in many educational institutions it is common even today to assign a public IP address to all networked devices including printers.</ref>. As of July 2016, the Shodan search engine categorizes only 31.264 internet-accessible devices as printers. Attacking intranet printers however may also be attractive to an insider. Imagine an employee who has motivation to obtain the department manager's payroll print job from a shared device. It is also worth mentioning that many new printers bring their own wireless access point – unencrypted by default to allow easy printing, for example via ''AirPrint'' <ref>''[https://support.apple.com/en-us/HT201311 About AirPrint]'', Apple Inc</ref> compatible mobile apps. While connecting to a printer through Wi-Fi requires the attacker to stay physically close to the device, it may be feasible to perform her attack from outside of the targeted institution depending on the signal strength. | Obviously, a port 9100 based attack requires IP packets to be routed from the attacker to the printer device and backwards but printers usually are not directly connected to the Internet <ref>It however must be noted that in many educational institutions it is common even today to assign a public IP address to all networked devices including printers.</ref>. As of July 2016, the Shodan search engine categorizes only 31.264 internet-accessible devices as printers. Attacking intranet printers however may also be attractive to an insider. Imagine an employee who has motivation to obtain the department manager's payroll print job from a shared device. It is also worth mentioning that many new printers bring their own wireless access point – unencrypted by default to allow easy printing, for example via ''AirPrint'' <ref>''[https://support.apple.com/en-us/HT201311 About AirPrint]'', Apple Inc</ref> compatible mobile apps. While connecting to a printer through Wi-Fi requires the attacker to stay physically close to the device, it may be feasible to perform her attack from outside of the targeted institution depending on the signal strength. | ||
Revision as of 19:54, 23 January 2017
Raw printing is what we define as the process of making a connection to port 9100/tcp of a network printer – a functionality which was originally introduced by HP in the early 90s using separate hardware modules. It is the default method used by CUPS and the Windows printing architecture [1] to communicate with network printers as it is considered as `the simplest, fastest, and generally the most reliable network protocol used for printers' [2]. Raw port 9100 printing, also referred to as JetDirect, AppSocket or PDL-datastream actually is not a printing protocol by itself. Instead all data sent is directly processed by the printing device, just like a parallel connection over TCP. In contrast to LPD, IPP and SMB interpreted printer control or page description languages can send direct feedback to the client, including status and error messages. Such a bidirectional channel is not only perfect for debugging, but gives us direct access to results of PJL, PostScript or PCL commands, for example for [information disclosure] attacks. Therefore raw port 9100 printing – which is supported by almost any network printer – is used as the channel for security analysis with PRET and PFT.
Who would put a printer on the Internet?
Obviously, a port 9100 based attack requires IP packets to be routed from the attacker to the printer device and backwards but printers usually are not directly connected to the Internet [3]. As of July 2016, the Shodan search engine categorizes only 31.264 internet-accessible devices as printers. Attacking intranet printers however may also be attractive to an insider. Imagine an employee who has motivation to obtain the department manager's payroll print job from a shared device. It is also worth mentioning that many new printers bring their own wireless access point – unencrypted by default to allow easy printing, for example via AirPrint [4] compatible mobile apps. While connecting to a printer through Wi-Fi requires the attacker to stay physically close to the device, it may be feasible to perform her attack from outside of the targeted institution depending on the signal strength.
→ Related aricles: Fundamentals, Attack carriers, PRET, PFT
- ↑ Windows Printer Driver Architecture, Microsoft Corporation
- ↑ Network Protocols supported by CUPS – AppSocket Protocol, M. Sweet
- ↑ It however must be noted that in many educational institutions it is common even today to assign a public IP address to all networked devices including printers.
- ↑ About AirPrint, Apple Inc